Develop an integrated IT Strategy by aligning your business processes, people and technology
Services - IT Advisory
Business Enablement Solutions
Systematic management for all of your IT investments. From applications to hardware, training and management processes.
We pride ourselves on strengthening our clients’ IT capabilities through thorough review and analysis of your current business processes and systems. We deliver custom standards and guidelines that lead to increased operational efficiency, decreased costs and reduced risks.
Achieve your key business objectives when SMAC Apps becomes an extension of your team.
Do you have a question about building a better IT Advisory?
Ask Us TodayServices - Consulting/Enterprise Solutions
Stay up to date with the latest digital technologies, changing business models and ever-growing customer expectations when SMAC Apps becomes an extension of your team.
Our customized enterprise solutions will help you solve business problems by identifying optimal technologies and future-proof roadmaps that lead to success. See below for how we can help you toward immediate ROI.
HOW CAN WE HELP?
Custom Solutions
SMAC Apps team will meet with your organization’s key participants, review current systems, and devise the best solution that meets your desired results and budget.
Web and Social Media
Our expert web design team and SEO professionals review the goals you want to accomplish with your online persona and build a meaningful and integrated online presence that will move your business to the forefront.
eCommerce
Our proficient team works with you to develop an integrated process to tie your website to your fulfillment and shipping departments, keeping your sales and marketing team running effortlessly.
Mobile Solutions
SMAC Apps has extensive experience in developing mobile applications for iOS, Android, smart phones, tablets and other portable devices. We develop mobile apps that integrate with your internal systems and seamlessly work across devices in this spectrum.
Managed Services
Looking for a reliable Managed Service Provider? SMAC Apps has been successfully helping small and medium sized businesses for more than a decade! Schedule a free consultation with SMAC Apps to find out if your company can benefit from outsourcing. Know more for further details.
IT Advisory
Technology continues to change and advance at a rapid pace. New software and applications could greatly enhance a business’s productivity, work flow, revenue stream, and more. If a company doesn’t take advantage of improved tech, it could get left behind the competition. To know more about how we can assist with your IT Advisory, Know more
The SMAC Apps team’s vast knowledge and many years of extensive project management and software implementation experience have helped numerous clients:
- We have rescued troubled projects and brought them back on track, helping their team succeed by meeting goals and staying within the timeframe and budget.
- We’ve created integrated systems that have improved productivity.
- Our team has built unique sites that integrate various ecommerce add-ons that helped grow customer interaction and sales.
- And more…
If you have an Enterprise IT problem, we have a solution.
Let's Talk
Services - Cybersecurity
43% of cyber attacks are against small businesses
Ask a Cyber SMEThe cyber threat to small and medium businesses (SMBs) is more financially damaging than the combined threat of fire, flood, and transport strikes.
While the vast majority of reported cybersecurity breaches over the past 18 months have concerned large and well-known companies across the globe, it is small and medium size businesses that are increasingly in the criminal’s cross-hairs.
According to a study by the Ponemon Institute, three in five SMBs have experienced a cyber attack in the last 12 months and one in three believe they are not capable of fending off an attack.
Cybersecurity custome solutions
Custom Solutions
Join our community of cybersecurity thought leaders, practitioners, students, and enthusiasts. Share your thoughts, tips, and tools for information security, cybersecurity, risk management, cybercrime, careers, privacy, etc..
JoinStart Protecting Your Business Against Cyber Attack
Technology is an enabler, giving business the ability to operate faster and more efficiently than ever before. Doing business in this fast paced and complex environment places additional pressure on business and technology leaders to not only learn how to navigate this new landscape but also how to protect themselves in this ever-changing environment. Today’s cyber security landscape is more complex than ever before but, that should’t not stop you from getting stated. Regardless of the size of your business or your technical ability there are some basic steps you can take improve your cyber defenses.
Our Services
Cybersecurity Our services
Implementing a well-defined and robust security program that is tailored to the specific needs of your business helps to ensure the confidentiality, integrity, availability and privacy of your data and that of your customers. Our advisory services is focused on working with business and technology leaders to develop and implement security programs. Our consultants will develop a comprehensive program and implementation roadmap based on accepted industry best practices and the specific needs of your business.

Our Standard Approach Includes:
- Collecting and analyzing information to understand the goals and objectives of the business, understanding the acceptable risk appetite and tolerance levels of the business.
- Reviewing existing security programs, plans, policies, procedures and controls to determine whether or not security goals and objectives are aligned with those of the business and industry.
- Performing a high-level security assessment to identify the current security posture of the business, high-risk threats and vulnerabilities.
- Working closely with the business and technology leaders to define a security capability maturity level target that is based on the existing capabilities and needs of the business.
- Identifying gaps between the current state capabilities and what is required to achieve the target maturity level.
- Identifying the people, policies, procedures, processes, controls and technologies required to achieve the target maturity level.
- Developing a phased implementation plan and roadmap.
A critical element in any Information Security Program is how well the organization manages risks. Managing risk involves the identification, assessment, treatment, monitoring and tracking of risk. Since it’s impossible to manage what you don’t know exists, it’s critical to begin any attempt to manage risk by performing a risk assessment to identify, estimate and prioritize the risks to organization’s information assets. To ensure a comprehensive assessment is performed, it’s important to include people, processes and technology in the assessment. Our consultants will develop conduct a Risk Assessment that is tailored to the specific needs of your business and industry.

Our standard approach includes:
- Compiling a list of the information assets of the organization.
- Preforming a business impact analysis to understand the true value of each asset.
- Creating risk scenarios to identify threats and vulnerabilities.
- Combining qualitative and quantitative approaches to estimate the likelihood and potential impact of the risk.
- Providing recommendations of how to treat the risk (Avoid, Transfer, Mitigate, Accept).
- Delivery of a Risk Register that documents each risk, likelihood, impact, prioritization of each risk.
Employees are a major part of an organization’s attack surface and remain the greatest vulnerability to cybersecurity, frequently targeted by attackers. Ensuring that employees have the knowledge and skills to defend themselves and the organization against threats is an essential part of any security program and a requirement for those organizations that need to comply with government and industry regulations, such as FISMA, PCI, HIPAA or Sarbanes-Oxley. A good security awareness program will educate employees on corporate policies, procedures, standards, guidelines and industry best practices for working with information technology. A critical (yet often overlooked) component of security awareness training is what to do in the event of a data breach. The minutes and hours following the discovery of a data breach are critical to not only preventing the attack from spreading but also to preserving the environment for forensic examination. Our consultants will develop a comprehensive security awareness training program and provide training that is designed specifically for your business.

Our standard approach includes:
- Designing a program that is compliant with the laws and regulations that apply to your business.
- Covering all the basics including physical security, password security, anti-phishing, social engineering.
- Providing training that is role based and includes all roles within the organization
- Diversifying the training content and delivery methods that include instructor lead sessions, self-paced training, simulations, games.
- Making the training intriguing and entertaining.
An Information security audit is a structured, systematic and measurable technical assessment of how the organization’s security policy is employed. It is part of the on-going process of defining and maintaining effective security policies. Security audits provide a fair and measurable way to examine how secure an organization is, by performing a security audit your organization can identify and remediate risk before they are compromised. Let our consultants perform a full security audit to uncover weaknesses and security gaps that exist within your organization and uncover the cause of noncompliance to establish an effective security program.

Our standard approach includes:
- Assessing security policies, procedures and controls to determine their operating effectiveness
- Conducting Penetration testing
- Auditing firewall configurations, website code and mobile applications
- Identifying internal control and regulatory deficiencies that could put the organization at risk.
- The delivery of a detail audit report
One of the most common and simplest ways a cybercriminal can gain access to your systems and applications is by exploiting known software vulnerabilities on your workstations. There are roughly 30-40 new software vulnerabilities published each day!
While most organizations know their endpoint devices are at risk, many fail to implement adequate security measures due to a lack of time, resources or budget constraints.
Our Endpoint Management Service allows you to outsource all the heavy lifting involved with managing these devices while retaining visibility and transparency across your enterprise.

Our Services Include:
Cybersecurity Vulnerability Management
Vulnerability Management
- Get continuous risk assessment without impacting system or network resources
- Gain insight into the security posture and align the enterprise with the security policies of the organization
- Automatically remediate risks
Patch Management
- Identify and roll out patches automatically
- Keep all major operating systems (Windows, Linux and Mac OS X) as well as third-party applications up-to-date
- Detect and fix configuration deviations, such as password polices and encryption strength
Compliance Management
- Achieve compliance to regulatory standards
- PCI, HIPAA, NIST 800-171, NIST 800-53
- Custom configuration standards
- Fix compliance deviations automatically to ensure that your organization is continuously compliant
Asset Management
- Track software and hardware assets
- Track new installations and changes to configuration settings
- Manage and optimize software licenses and costs
- Blacklist rogue applications that show up in the inventory
Endpoint Management
- Get visibility into the status of endpoint systems, with 100s of built-in checks
- Gather network details and map of devices
- Search for the presence of sensitive data, such as credit card information, soial security numbers, etc.
- Deploy software, block applications and devices
Threat Detection & Response
- Detect Indicators of Attack(IoA) and Indicators of Compromise(IoC)
- Run queries to check for abnormal behavior or unusual network activity that is symptomatic of an attack
- Stop on-going attacks by blocking applications, killing processes, cleaning up startup folders
Our services
Clients

Assess & Plan

Educate & Prepare

Monitor & Measure
Implementing a well-defined and robust security program that is tailored to the specific needs of your business helps to ensure the confidentiality, integrity, availability and privacy of your data and that of your customers. Our advisory services is focused on working with business and technology leaders to develop and implement security programs. Our consultants will develop a comprehensive program and implementation roadmap based on accepted industry best practices and the specific needs of your business.
Our Standard Approach Includes:
- Collecting and analyzing information to understand the goals and objectives of the business, understanding the acceptable risk appetite and tolerance levels of the business.
- Reviewing existing security programs, plans, policies, procedures and controls to determine whether or not security goals and objectives are aligned with those of the business and industry.
- Performing a high-level security assessment to identify the current security posture of the business, high-risk threats and vulnerabilities.
- Working closely with the business and technology leaders to define a security capability maturity level target that is based on the existing capabilities and needs of the business.
- Identifying gaps between the current state capabilities and what is required to achieve the target maturity level.
- Identifying the people, policies, procedures, processes, controls and technologies required to achieve the target maturity level.
- Developing a phased implementation plan and roadmap.

A critical element in any Information Security Program is how well the organization manages risks. Managing risk involves the identification, assessment, treatment, monitoring and tracking of risk. Since it’s impossible to manage what you don’t know exists, it’s critical to begin any attempt to manage risk by performing a risk assessment to identify, estimate and prioritize the risks to organization’s information assets. To ensure a comprehensive assessment is performed, it’s important to include people, processes and technology in the assessment. Our consultants will develop conduct a Risk Assessment that is tailored to the specific needs of your business and industry.
Our standard approach includes:
- Compiling a list of the information assets of the organization.
- Preforming a business impact analysis to understand the true value of each asset.
- Creating risk scenarios to identify threats and vulnerabilities.
- Combining qualitative and quantitative approaches to estimate the likelihood and potential impact of the risk.
- Providing recommendations of how to treat the risk (Avoid, Transfer, Mitigate, Accept).
- Delivery of a Risk Register that documents each risk, likelihood, impact, prioritization of each risk.

Employees are a major part of an organization’s attack surface and remain the greatest vulnerability to cybersecurity, frequently targeted by attackers. Ensuring that employees have the knowledge and skills to defend themselves and the organization against threats is an essential part of any security program and a requirement for those organizations that need to comply with government and industry regulations, such as FISMA, PCI, HIPAA or Sarbanes-Oxley. A good security awareness program will educate employees on corporate policies, procedures, standards, guidelines and industry best practices for working with information technology. A critical (yet often overlooked) component of security awareness training is what to do in the event of a data breach. The minutes and hours following the discovery of a data breach are critical to not only preventing the attack from spreading but also to preserving the environment for forensic examination. Our consultants will develop a comprehensive security awareness training program and provide training that is designed specifically for your business.
Our standard approach includes:
- Designing a program that is compliant with the laws and regulations that apply to your business.
- Covering all the basics including physical security, password security, anti-phishing, social engineering.
- Providing training that is role based and includes all roles within the organization
- Diversifying the training content and delivery methods that include instructor lead sessions, self-paced training, simulations, games.
- Making the training intriguing and entertaining.

An Information security audit is a structured, systematic and measurable technical assessment of how the organization’s security policy is employed. It is part of the on-going process of defining and maintaining effective security policies. Security audits provide a fair and measurable way to examine how secure an organization is, by performing a security audit your organization can identify and remediate risk before they are compromised. Let our consultants perform a full security audit to uncover weaknesses and security gaps that exist within your organization and uncover the cause of noncompliance to establish an effective security program.
Our standard approach includes:
- Assessing security policies, procedures and controls to determine their operating effectiveness
- Conducting Penetration testing
- Auditing firewall configurations, website code and mobile applications
- Identifying internal control and regulatory deficiencies that could put the organization at risk.
- The delivery of a detail audit report

One of the most common and simplest ways a cybercriminal can gain access to your systems and applications is by exploiting known software vulnerabilities on your workstations. There are roughly 30-40 new software vulnerabilities published each day!
While most organizations know their endpoint devices are at risk, many fail to implement adequate security measures due to a lack of time, resources or budget constraints.
Our Endpoint Management Service allows you to outsource all the heavy lifting involved with managing these devices while retaining visibility and transparency across your enterprise.
Our Services Include:
Cybersecurity Vulnerability Management
Vulnerability Management
- Get continuous risk assessment without impacting system or network resources
- Gain insight into the security posture and align the enterprise with the security policies of the organization
- Automatically remediate risks
Patch Management
- Identify and roll out patches automatically
- Keep all major operating systems (Windows, Linux and Mac OS X) as well as third-party applications up-to-date
- Detect and fix configuration deviations, such as password polices and encryption strength
Compliance Management
- Achieve compliance to regulatory standards
- PCI, HIPAA, NIST 800-171, NIST 800-53
- Custom configuration standards
- Fix compliance deviations automatically to ensure that your organization is continuously compliant
Asset Management
- Track software and hardware assets
- Track new installations and changes to configuration settings
- Manage and optimize software licenses and costs
- Blacklist rogue applications that show up in the inventory
Endpoint Management
- Get visibility into the status of endpoint systems, with 100s of built-in checks
- Gather network details and map of devices
- Search for the presence of sensitive data, such as credit card information, soial security numbers, etc.
- Deploy software, block applications and devices
Threat Detection & Response
- Detect Indicators of Attack(IoA) and Indicators of Compromise(IoC)
- Run queries to check for abnormal behavior or unusual network activity that is symptomatic of an attack
- Stop on-going attacks by blocking applications, killing processes, cleaning up startup folders

Cybersecurity Maturity Model Certification – CMMC
Subscribe for CMMC Updates
What is the CMMC?
The Office of the Under Secretary of Defense for Acquisition & Sustainment (OUSD(A&S) has been working with DoD stakeholders, University Affiliated Research Centers (UARCs), Federally Funded Research and Development Centers (FFRDC), and industry to develop a new requirement for existing DoD contractors, replacing the current self-attestation model.
The new model released by the Department of Defense (DoD) is the Cybersecurity Maturity Model Certification (CMMC). The intent of the CMMC is to ensure appropriate levels of cybersecurity controls and processes are adequate and in place to protect controlled unclassified information (CUI) on the Defense Industrial Base (DIB).
The DoD is planning to migrate to the new CMMC framework in 2020. The CMMC will serve as a verification mechanism to ensure appropriate levels of cybersecurity practices and processes are in place to protect controlled unclassified information (CUI) that resides on the Department’s industry partners’ networks. CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide services requires or permits an agency to handle using safeguarding or dissemination controls. CUI resources, including online training to better understand CUI can be found on National Archives’ website.
The intent of the CMMC is to combine various cybersecurity control standards such as NIST SP 800-171, NIST SP 800-53, ISO 27001, ISO 27032, AIA NAS9933 and others into one unified standard for cybersecurity. In addition to cybersecurity control standards, the CMMC will also measure the maturity of a company's institutionalization of cybersecurity practices and processes. The CMMC encompasses multiple maturity levels that ranges from "Basic Cybersecurity Hygiene" to "Advanced".
Why the DoD Created The CMMC
The introduction of the CMMC is the latest step by the Department of Defense (DoD) to mandate that private DoD Contractors adopt cybersecurity standards and practices as part of the government-led effort to protect the U.S. defense supply chain from foreign and domestic cyber threats, and reduce the overall security risk of the sector.
Highlights of the CMMC
- A single standard used across all DoD contracts starting in 2020-2021
- The required CMMC level will be contained in RFP sections L & M starting midyear 2020
- All DoD Contractors will need to become CMMC Certified by passing a CMMC Audit to verify they have met the appropriate level of cybersecurity for their business. This will be a "go/no-go" requirement for any organization who wants to hold contracts with the Department of Defense.
- Self-certification is not allowed. A certified independent 3rd party organization will conduct the audit.
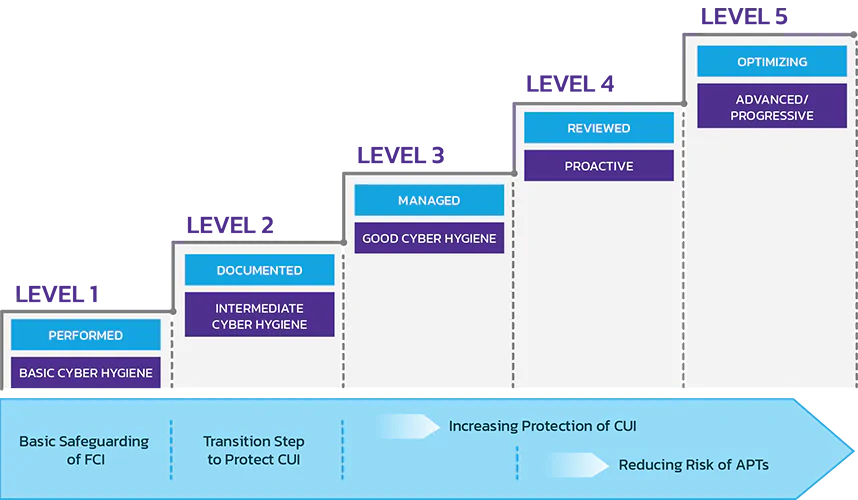
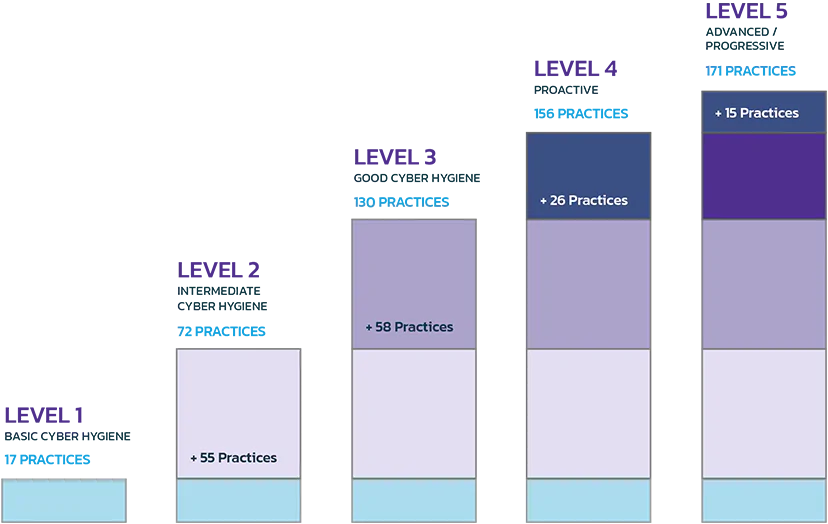
- The CMMC consists of 5 levels from basic hygiene (Level 1) to advanced (Level 5). Most RFPs are expected to require a Level 1 to Level 3 certification.
- The certification cost has not yet been determined. The cost, and associated assessment will likely scale with the level requested.
- The goal is for CMMC to be cost-effective and affordable for small businesses to implement at the lower CMMC levels.
Summary of CMMC Levels
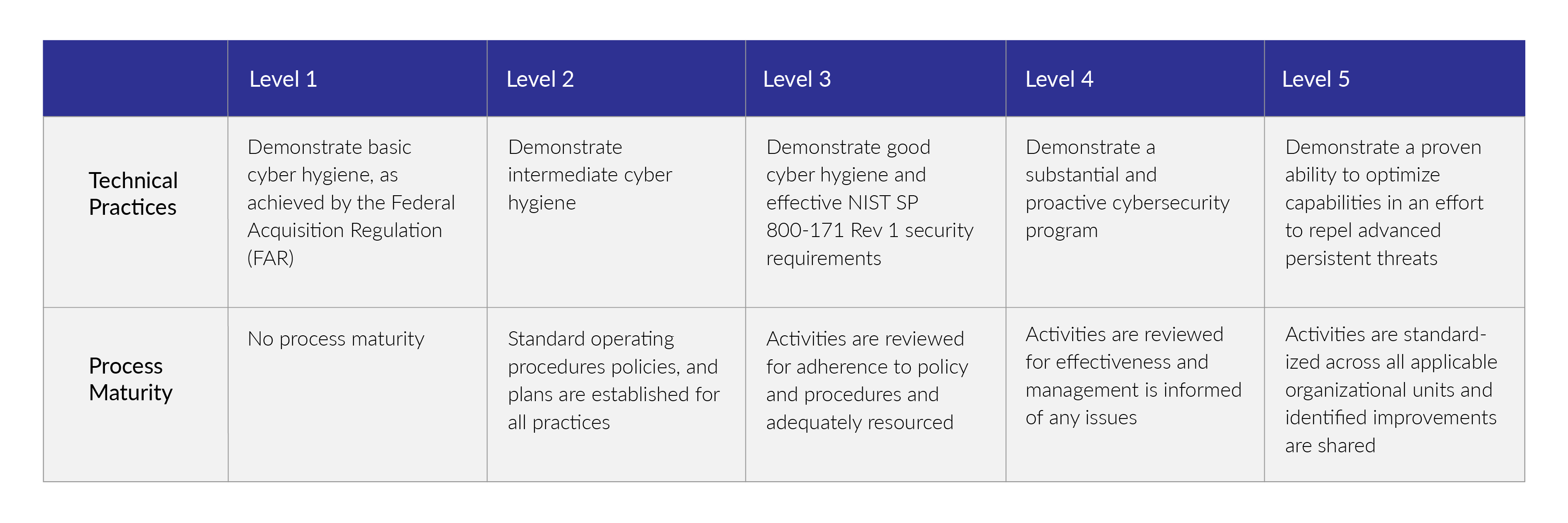
CMMC Domains
The CMMC model consists of 17 domains. The majority of these CMMC domains originated from the Federal Information Processing Standard (FIPS) and the NIST SP 800-171.
Practice Levels
Practices
What you need to know
Even if your organization does not handle Controlled Unclassified Information (CUI), all companies conducting business with the DoD must be certified. The level of certification required will depend upon the amount of CUI a company handles or processes.
- The government will determine the appropriate tier of certification for the contracts they administer. The required CMMC level will be contained in sections L & M of the Request for Proposals (RFP).
- All DoD Contractors will need to become CMMC Certified by passing a CMMC Audit to verify they have met the appropriate level of cybersecurity for their business.
- There is no self-certification. Certifications will only be credited through CMMC Audits.
- Your company will coordinate directly with an accredited and independent third-party commercial certification organization to perform the CMMC assessment. Your company will specify the level of the certification requested based on your company’s specific business requirements.
- Certification will be awarded at the appropriate CMMC level upon demonstrating the appropriate maturity in capabilities and organizational maturity to the satisfaction of the assessor and certifier.
- The certification cost has not yet been determined. The cost and associated assessment will likely scale with the level requested. The cost of certification will be considered an allowable, reimbursable cost and will not be prohibitive.
- Your certification level will be made public; however, details regarding specific findings will not be publicly accessible. The DoD will see your certification level.
- The duration of a certification is still under consideration.
- If your company is certified and your company is compromised, you will not lose your certification. However, depending on the circumstances of the compromise and the direction of the government program manager, you may be required to be recertified.
- Engage a partner like SMAC Apps to assist with pre-certification readiness. We’ll partner with you to determine your high-level maturity level, establish hygiene best practices, and implement a cybersecurity program to prepare your organization. Contact us now to learn how SMAC Apps can help.
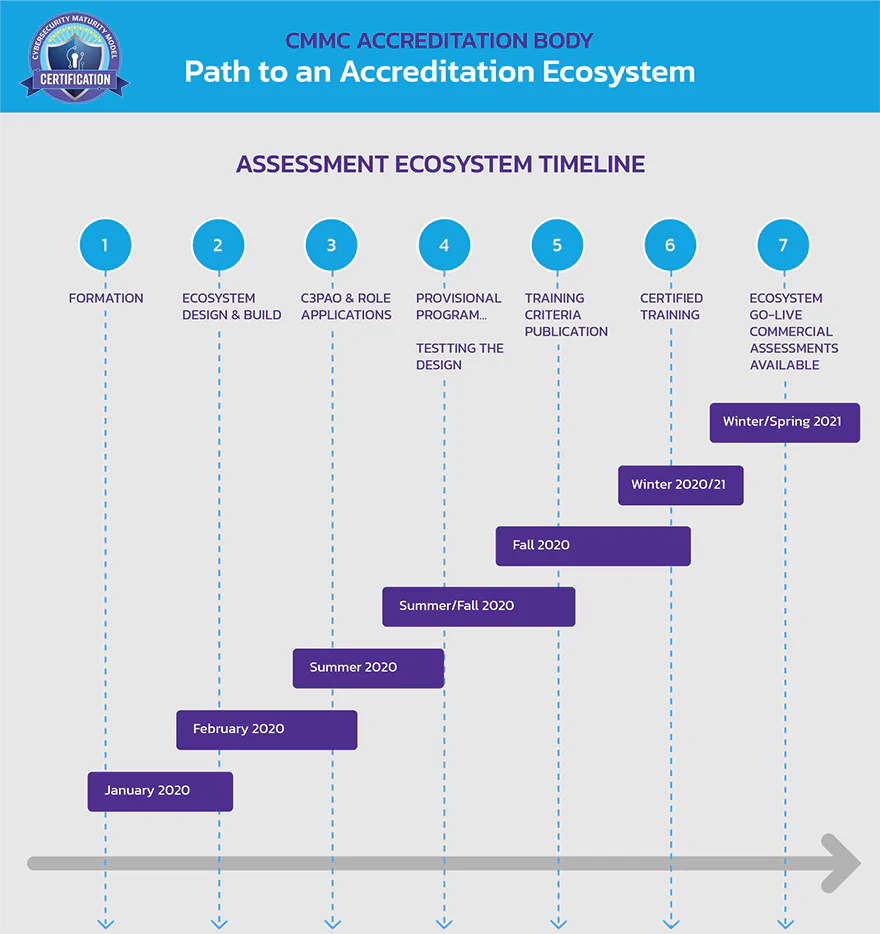
Important Dates
Version 0.7 of the CMMC framework was released on December 6th, 2019. This version includes CMMC Levels 1-5 as well as the associated discussion and clarification for a subset of practices and processes. In June 2020, industry should begin to see the CMMC requirements as part of Requests for Information. The initial implementation of the CMMC will only be within the DoD.
- Winter/Sprint 2020/2021 – EcoSystem Go Live
- Winter 2020/2021 – Certified Training
- Fall 2020 – Training Criteria Published
- September 2, 2020 - CMMC-AB Approves First 11 Licensed Partner Publishers (LPPs) to Deliver Certification Curriculum
- August 31, 2020 – CMMC-AB announced that it has signed an MOU with Dun & Bradstreet to provide, as a partner, financial and ownership background checks for the organizations applying for accreditation by the CMMC-AB.
- January 30, 2020 – CMMC Model v1.0 released
- January 27, 2020 – CMMC Accrediting Body Board of Directors announced
- December 6, 2019 – CMMC version v0.7 released
- December 4, 2019 – Accreditation Body follow-up meeting held
- November 19, 2019 – Accreditation Body kickoff meeting held
- November 8, 2019 – CMMC version v0.6 released
- October 10, 2019 – CMMC Accreditation Body RFI
- September 5, 2019 – CMMC version v0.4 released
References
- Understanding CUI – https://www.archives.gov/cui/training.html
- Securing Defense – Critical Supply Chains https://www.ndia.org/-/media/sites/services-issues/cmmc-brief—5-jun-19.ashx?la=en
- CMMC website – https://dodcio.defense.gov/CMMC/
- CMMC FAQs – https://dodcio.defense.gov/CMMC/FAQ/
- The Cybersecurity Maturity Model Certification Accreditation Body (CMMC-AB) website - https://dodcio.defense.gov/CMMC/
- Download CMMC version v2.0 - https://dodcio.defense.gov/CMMC/
Contacting Us
https://smacappsqa.ezysubscribe.com/
2 Research Way, Princeton, NJ 08540
609-212-0524
[email protected]
Please subscribe for the latest updates Subscribe
Please register to our Cybersecurity Community Register
Services - Managed Services
Adopting IT managed services is intended to be an efficient way to stay up-to-date on technology, have access to skills and address issues related to cost, quality of service and risk.
Being an accomplished Managed It Service provider, through our breadth of knowledge in diverse business industries and latest technologies, we help you in keeping your IT environment running smoothly. From software updates, configurations, Application optimization, Outsourced Center of Technology (CTO) services, and IT asset management; SMAC Apps offers customized IT solutions to fit your company needs. Our experience covers large corporations through small business.
Some of our services include:
- OS/Software Implementation and Integration
- Center of Technology Staffing for Small and Mid-Sized Businesses
- CTO Managed Service
- Digital Marketing/SEO
- Network and System Monitoring
- Data Center Optimization
- Customized Requirements
In the broadest sense, Managed Services allow a company to concentrate on their core business while the IT Managed Service provider tends to all or designated segments of the IT operation. There may be portions of the computer environment that are requiring additional expertise or consume too much time that might be better spent in other areas of the business.
The time frame for a managed service is dependent on the needs of the organization. A shorter period of time can set up a Build, Operate, and Transfer model for software testing. A long-term time frame would be more suitable for SEO and Digital Marketing monitoring and development. Mid length assistance would be fitting for assistance with a complicated OS or upgrade deployment.
Our goal is to assure you have the right service for the right timeframe to bring you success.
Ask How We Can HelpServices - Digital Marketing
SMAC Apps Digital Marketing team can pull up your website rankings, while increasing your overall response and interactivity rate. Our suite of interrelated Digital Marketing services, which encompass SEO services, Online Reputation Management, internet marketing, and more, can bring your business the attention it needs – and deserves.
DO YOU FEEL LOST WHEN …
- You’re opening a new business in a highly competitive field and don’t know where to start with social media marketing? You know it needs updating, but what do you need and how do you get seen?
- Your reputation is being damaged online. How do you rise above the negative?
- The website you have is looking outdated, isn’t responsive to different devices, and doesn’t address the changing needs of your clients? How do you go about developing a strong, visible, interactive site?
- Your website traffic suddenly starts to decrease and you don’t understand why or how to improve it? Why are you no longer reaching your target market?
Whether your company is B2B or B2C, as your trusted partner our Digital Marketing Agency team will work with you and develop a plan to help you accelerate your business growth and success.
Contact Us For More InfoServices - E-Commerce Solutions
Over 60% of the people begin their shopping experience online.
If your business isn’t selling online, it’s missing a huge potential market. But starting or revamping an online store can be intimidating. If you want to take advantage of the power of the internet, it’s important to have a smooth e-Commerce solution that entices customers and provides you with the analytics you need to meet demand and quickly adjust to trends. SMAC Apps e-Commerce Solutions team makes sure your online potential is being reached by building a detailed plan based on your needs and goals.
We can build you a strong E-Commerce System:
- Increases customer engagement and helps build a broader client base.
- Convenient and intuitive for customers – and employees!
- Provides your business with expanded marketing opportunities through SEO and social media integration.
- Scalable to grow or change as your business changes.
The e-commerce sector is booming. Retail companies across the board are doubling down on their digital-sales presence. A rapidly shifting landscape requires flexible, up-to-date, and service-oriented IT support. Through its relationships with retailers and 3PL partners, SMAC Apps is deeply versed in e-commerce IT requirements and builds flexible systems that can adapt to evolving circumstances. SMAC Apps e-Commerce platform is integrated with Inventory & Warehouse Management, which is an end-to-end solution that can include logistics and shipping through our integrated partner Marketway.
Get your business growing
Call Us Today! InfoServices - Cloud Software Solutions
Clients
A successful cloud strategy can empower an organization with agility and resilience to build a high-performance business. A wrong cloud strategy could create the opposite effect.
SMAC Apps can help organizations build a proper cloud strategy by utilizing the appropriate environment (private clouds, public clouds and legacy IT environments) into a high-performance IT platform geared for innovation and growth.
Whether you’re building a Product, Application, or Hosting Business Applications, Data & Analytics or setting up dynamic virtual work desks, we can help you with the right strategy to capitalize on the advantages of Cloud.

cloud security

build on cloud

migrate to cloud

optimize your cloud
Cloud Security
SMAC Apps provides a comprehensive suite of security services that utilize best-in-class security services from Cloudflare, Imunify360, and GoDaddy Security Premium.
These security services protect the network, application, file, and operating system levels to prevent malware infections, web attacks, vulnerability exploitation, and other threats.
Key features include:
- Network and Web Application Firewalls to help prevent unauthorized access.
- Realtime malware scanning and reliable cleanup.
- HTTPS encryption (HTTP/S L4-7) to identify and mitigate distributed denial-of-service attacks.
- Intrusion Dection and Prevention monitoring of network traffic to identify malicious behavior and block attacks.
- Active Response OSSEC to prevent operating system intrusions.
- SSL certificate to authenticate website identity and enable encrypted connections.
- Real-time monitoring of logs that contain detailed information of alerts and perfromace.
- Proactive Patch Management to ensure systems are updated with security patches and updates.
- 24×7 active monitoring.
- Fast and Secure Managed DNS Service.
- Secure backup.
Build on Cloud
Build your application from the ground up in the Cloud. Different vendors offer multiple services which can help you rapidly build and deploy your applications and products. We help you find the right cloud strategy for your applications.
Migrate to Cloud
Cloud adoption is a key element for businesses to fire up their performance engines. Without the right plan there could be delays and a disruption in business. We become an advocate to the customer managing their migration.
Optimize your Cloud
When traditional applications are migrating to the cloud, some of the underlying technologies can’t accommodate the full benefits of being in the cloud. We can help you identify those bottlenecks and can optimize your systems, resulting in higher performance and cost savings.
Services - Data & Analytics
DO NOT LET THIS HAPPEN TO YOUR ORGANIZATION’S DATA.
SMAC Apps helps organizations consolidate their Data and Analytics Strategy to build a high-performance data driven organization. With 10+ years’ experience in deploying end-to-end Data and Analytics platforms, we have successfully built frameworks to accelerate the Data and Analytics journey.
Our team of experienced consultants, who have deep technology experience and industry knowledge, can engage across all of our service offerings – Advisory, Managed Services, Application implementation, Data Literacy, Analytics solutions.
We can work with any preferred technologies and platforms. We deliver the tools and technologies to ensure that analytics becomes a sustained competitive advantage for your business.

Services - Digital Accessibility
adopting digital accessibility for ada compliance
Being ADA compliant is more than just assuring your physical facility is accessible to everyone, it includes your digital presence as well. Providing accessibility is an ongoing journey. During the journey of technical accessibility, SMAC Apps will help your organization streamline the process, create policies and procedures, and make being technologically accessible a regular part of doing business.
How can you assure your digital footprint is in line with the Americans with Disabilities Act?
- Get an accessibility audit
- Train your team
- Support your content authors and software developers
- Create and adopt a formal accessibility services
- Provide support to people with disabilities
what is section 508 of the rehabilitation act of 1973?
ADA – American disabilities act, The Rehabilitation Act – was originally signed into law in 1973. It prohibits discrimination against people with disabilities in programs and services run by the federal government or its contractors and you are required to comply with federal conditions if you are a federal agency or run a program for the federal government. It has also become a standard for all businesses.
Section 508 covers technology procured by a federal agency under contract with a private entity or produced within the agency itself. It applies to all Digital Technology including software, web sites, web applications, and hardware applications such as computers, networks, peripherals, and other types of electronic office equipment.
how can smac apps help in your accessibility journey?
Whether you’re in the middle of accessibility remediation or planning for the future, it helps to bring in an expert. Our accessibility specialists can work alongside your team at any stage in the process to offer guidance and assistance and help you ensure a successful outcome.
Services - ServiceNow
Get the most of your ServiceNow investments when SMAC Apps becomes an extension of your team. Whether you’re looking to expand your service capabilities, decrease your time-to-market or improve IT customer satisfaction, we’ll be with you every step of the way.
Qualified Specialists
Industry-leading administration and maintenance support for new projects and updates. Work with SMAC Apps to experience talent that transforms.
Focus on your core business
When we become an extension of your team, we offer trusted and consistent guidance in key technology areas so you can focus on what matters most.
Secure IT Maintenance
Expand your capabilities with trusted, secure support to get the most out of your ServiceNow investments. We’ll support you through the update process for the latest ServiceNow releases.
Cost Savings
We optimize the way companies transform and impact the delivery of their IT. Saving you time and money.
Doing a world of social good
By choosing SMAC Apps to augment your ServiceNow team, you’re helping us grow organizations that give back to communities around the globe.







































































Case Studies
No posts found in this category.